Flexible Database Monitoring Architecture
The ideal solution for a DBA to monitor their database environment is one unhampered by limitations of the hardware supported by the product. Clearly, Surveillance DB has the flexibility to provide multiple configuration choices, creating the means to optimally monitor the database in any environment.
Flexible Agent Architecture
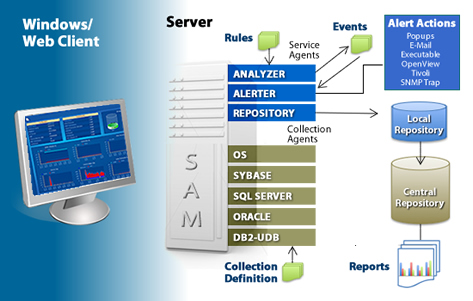
The Surveillance architecture is composed of the Session Agent Manager, called SAM, the Service Sub-Agents, Collections Sub-Agents, and the Wndows/Web Client. The SAM coordinates the agent activities and sends information to connected clients.
The collection agents connect to the supported database components to monitor the database(s), and the operating system. The collection sub-agents can connect from a system that is not running the database monitored components, we call this a virtual agent, or a term commonly described as "agentless". Agentless monitoring is helpful if the system running the database components is tight on resources or running a non-supported operating system.
The collection sub-agents can also connect directly from the system running the database monitored components which we call a native agent. Native connections have many advantages over virtual connections including better control of network resources and access to many more database metrics for monitoring and management.
The Service Sub-agents include the analyzer, alerter, and repos. The analyzer checks the collected data values against rules to determine if an event has occurred. The alerter processes the event and performs event actions. The Repository stores the data locally for data flashback and then forwards the data to a repository for centralized reporting. The client is used to configure collections, set up events, respond to alarms, and view performance data from the monitor. The client is not required for monitoring and alerting.
Rule-based Alerting and Event Architecture
Surveillance uses an extensive alerting and alarming facility that comes with a library of ready-to-use predefined rules. Rules are needed to activate the Session Agent Manager (SAM) which gathers data information, creates alerts based on requested thresholds and writes records to the local repository. Rules can be assigned for any supported database and OS. Additionally, User Defined Collections (UDCs) can be created for files and non-standard databases to utilize all of the product's SAM functionality. To ensure the network traffic is planned around peak system traffic loads, the information gathered is written to a local repository and remains until a scheduled request to copy to the central repository is made for reporting and trend analysis.